Lab architecture:
Create namespace for Harbor and copy there the secret with Let's Encrypt certificate:
kubectl create namespace harbor2-system
kubectl label namespace harbor2-system app=kubedCheck if the certificate generated by cert-manager in cert-manager namespace
was successfully copied to harbor2-system namespace:
kubectl get secrets ingress-cert-${LETSENCRYPT_ENVIRONMENT} -n harbor2-system -o json | jq ".metadata | .annotations, .labels"Output:
{
"certmanager.k8s.io/alt-names": "*.mylabs.dev",
"certmanager.k8s.io/common-name": "*.mylabs.dev",
"certmanager.k8s.io/ip-sans": "",
"certmanager.k8s.io/issuer-kind": "ClusterIssuer",
"certmanager.k8s.io/issuer-name": "letsencrypt-production-dns",
"kubed.appscode.com/origin": "{\"namespace\":\"cert-manager\",\"name\":\"ingress-cert-production\",\"uid\":\"3bda1a77-93f7-11e9-afeb-0aa3c1d9f47e\",\"resourceVersion\":\"15881\"}"
}
{
"certmanager.k8s.io/certificate-name": "ingress-cert-production",
"kubed.appscode.com/origin.cluster": "my_k8s_cluster",
"kubed.appscode.com/origin.name": "ingress-cert-production",
"kubed.appscode.com/origin.namespace": "cert-manager"
}Add Harbor Helm repository:
helm repo add harbor https://helm.goharbor.ioInstall Harbor using Helm:
helm ls | grep harbor2 || \
helm install --wait --name harbor2 --namespace harbor2-system harbor/harbor --version v1.1.1 \
--set expose.ingress.hosts.core=core2.${MY_DOMAIN} \
--set expose.ingress.hosts.notary=notary2.${MY_DOMAIN} \
--set expose.tls.secretName=ingress-cert-${LETSENCRYPT_ENVIRONMENT} \
--set persistence.enabled=false \
--set externalURL=https://core2.${MY_DOMAIN} \
--set harborAdminPassword=adminLogin to Argo CD:
argocd login --insecure argocd-grpc.${MY_DOMAIN} --username admin --password adminOutput:
'admin' logged in successfully
Context 'argocd-grpc.mylabs.dev' updated
Create new harbor project:
argocd --insecure --server argocd-grpc.${MY_DOMAIN} proj create harbor --description "Harbor project" --dest https://kubernetes.default.svc,harbor-system --src https://github.com/goharbor/harbor-helm.gitCreate namespace for Harbor and copy there the secrets with Let's Encrypt certificate:
kubectl create namespace harbor-system
kubectl label namespace harbor-system app=kubedDeploy Harbor:
argocd --insecure --server argocd-grpc.${MY_DOMAIN} app create harbor \
--auto-prune \
--dest-namespace harbor-system \
--dest-server https://kubernetes.default.svc \
--path . \
--project harbor \
--repo https://github.com/goharbor/harbor-helm.git \
--revision v1.1.1 \
--sync-policy automated \
-p database.type=external \
-p database.external.host=pgsql.${MY_DOMAIN} \
-p database.external.username=harbor_user \
-p database.external.password=harbor_user_password \
-p database.external.coreDatabase=harbor-registry \
-p database.external.clairDatabase=harbor-clair \
-p database.external.notaryServerDatabase=harbor-notary_server \
-p database.external.notarySignerDatabase=harbor-notary_signer \
-p expose.ingress.hosts.core=core.${MY_DOMAIN} \
-p expose.ingress.hosts.notary=notary.${MY_DOMAIN} \
-p expose.tls.secretName=ingress-cert-${LETSENCRYPT_ENVIRONMENT} \
-p externalURL=https://core.${MY_DOMAIN} \
-p harborAdminPassword=admin \
-p persistence.resourcePolicy=delete \
-p persistence.persistentVolumeClaim.registry.size=1Gi \
-p persistence.persistentVolumeClaim.chartmuseum.size=1GiOutput:
application 'harbor' created
Check the status of the Harbor application and wait until it's fully initialized:
argocd --server argocd-grpc.${MY_DOMAIN} app wait --health harborOutput:
TIMESTAMP GROUP KIND NAMESPACE NAME STATUS HEALTH HOOK MESSAGE
...
2019-06-05T14:35:15+02:00 apps Deployment harbor-system harbor-harbor-chartmuseum Synced Healthy deployment.apps/harbor-harbor-chartmuseum created
2019-06-05T14:35:18+02:00 apps StatefulSet harbor-system harbor-harbor-redis Synced Healthy statefulset.apps/harbor-harbor-redis created
2019-06-05T14:35:24+02:00 apps Deployment harbor-system harbor-harbor-registry Synced Healthy deployment.apps/harbor-harbor-registry created
2019-06-05T14:35:24+02:00 apps Deployment harbor-system harbor-harbor-clair Synced Healthy deployment.apps/harbor-harbor-clair created
2019-06-05T14:36:27+02:00 apps Deployment harbor-system harbor-harbor-core Synced Healthy deployment.apps/harbor-harbor-core created
Name: harbor
Project: harbor
Server: https://kubernetes.default.svc
Namespace: harbor-system
URL: https://argocd-grpc.mylabs.dev/applications/harbor
Repo: https://github.com/goharbor/harbor-helm.git
Target: v1.1.0
Path: .
Sync Policy: Automated (Prune)
Sync Status: Synced to v1.1.0 (223528d)
Health Status: Healthy
GROUP KIND NAMESPACE NAME STATUS HEALTH
apps Deployment harbor-system harbor-harbor-registry Synced Healthy
Service harbor-system harbor-harbor-clair Synced Healthy
Service harbor-system harbor-harbor-notary-signer Synced Healthy
apps Deployment harbor-system harbor-harbor-chartmuseum Synced Healthy
Service harbor-system harbor-harbor-portal Synced Healthy
apps Deployment harbor-system harbor-harbor-core Synced Healthy
ConfigMap harbor-system harbor-harbor-registry Synced Healthy
Service harbor-system harbor-harbor-core Synced Healthy
Service harbor-system harbor-harbor-notary-server Synced Healthy
Service harbor-system harbor-harbor-jobservice Synced Healthy
apps Deployment harbor-system harbor-harbor-clair Synced Healthy
apps Deployment harbor-system harbor-harbor-portal Synced Healthy
Secret harbor-system harbor-harbor-chartmuseum Synced Healthy
ConfigMap harbor-system harbor-harbor-core Synced Healthy
PersistentVolumeClaim harbor-system harbor-harbor-registry Synced Healthy
ConfigMap harbor-system harbor-harbor-chartmuseum Synced Healthy
ConfigMap harbor-system harbor-harbor-notary-server Synced Healthy
PersistentVolumeClaim harbor-system harbor-harbor-jobservice Synced Healthy
apps Deployment harbor-system harbor-harbor-notary-signer Synced Healthy
apps StatefulSet harbor-system harbor-harbor-redis Synced Healthy
ConfigMap harbor-system harbor-harbor-clair Synced Healthy
Service harbor-system harbor-harbor-chartmuseum Synced Healthy
Service harbor-system harbor-harbor-redis Synced Healthy
apps Deployment harbor-system harbor-harbor-jobservice Synced Healthy
extensions Ingress harbor-system harbor-harbor-ingress Synced Healthy
Secret harbor-system harbor-harbor-jobservice Synced Healthy
Secret harbor-system harbor-harbor-registry Synced Healthy
Service harbor-system harbor-harbor-registry Synced Healthy
apps Deployment harbor-system harbor-harbor-notary-server Synced Healthy
Secret harbor-system harbor-harbor-core Synced Healthy
ConfigMap harbor-system harbor-harbor-jobservice Synced Healthy
PersistentVolumeClaim harbor-system harbor-harbor-chartmuseum Synced Healthy
ArgoCD - Applications:
ArgoCD - Application Details:
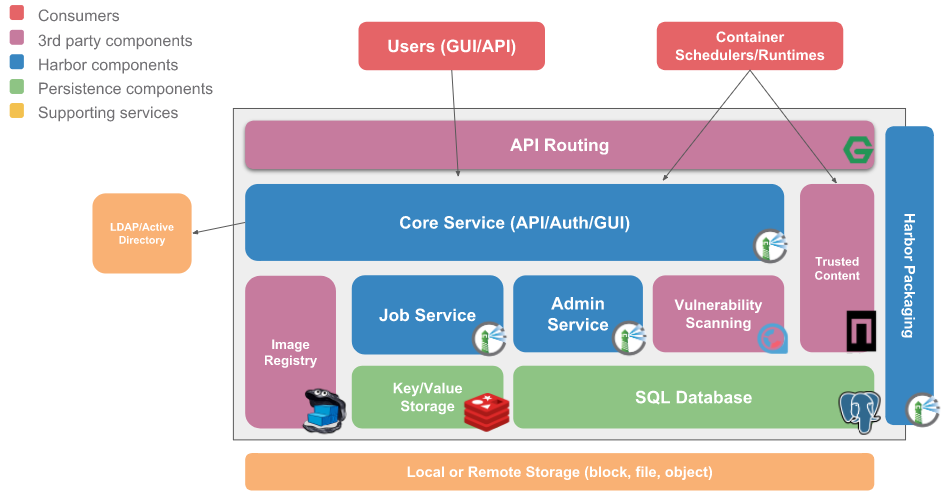
Harbor architecture:
Check how the Harbor Ingress looks like:
kubectl describe ingresses -n harbor-system harbor-harbor-ingressOutput:
Name: harbor-harbor-ingress
Namespace: harbor-system
Address: 54.93.44.33
Default backend: default-http-backend:80 (<none>)
TLS:
ingress-cert-production terminates core.mylabs.dev
ingress-cert-production terminates notary.mylabs.dev
Rules:
Host Path Backends
---- ---- --------
core.mylabs.dev
/ harbor-harbor-portal:80 (192.168.70.197:80)
/api/ harbor-harbor-core:80 (192.168.86.6:8080)
/service/ harbor-harbor-core:80 (192.168.86.6:8080)
/v2/ harbor-harbor-core:80 (192.168.86.6:8080)
/chartrepo/ harbor-harbor-core:80 (192.168.86.6:8080)
/c/ harbor-harbor-core:80 (192.168.86.6:8080)
notary.mylabs.dev
/ harbor-harbor-notary-server:4443 (192.168.25.61:4443)
Annotations:
ingress.kubernetes.io/proxy-body-size: 0
ingress.kubernetes.io/ssl-redirect: true
kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"extensions/v1beta1","kind":"Ingress","metadata":{"annotations":{"ingress.kubernetes.io/proxy-body-size":"0","ingress.kubernetes.io/ssl-redirect":"true","nginx.ingress.kubernetes.io/proxy-body-size":"0","nginx.ingress.kubernetes.io/ssl-redirect":"true"},"labels":{"app":"harbor","app.kubernetes.io/instance":"harbor","chart":"harbor","heritage":"Tiller","release":"harbor"},"name":"harbor-harbor-ingress","namespace":"harbor-system"},"spec":{"rules":[{"host":"core.mylabs.dev","http":{"paths":[{"backend":{"serviceName":"harbor-harbor-portal","servicePort":80},"path":"/"},{"backend":{"serviceName":"harbor-harbor-core","servicePort":80},"path":"/api/"},{"backend":{"serviceName":"harbor-harbor-core","servicePort":80},"path":"/service/"},{"backend":{"serviceName":"harbor-harbor-core","servicePort":80},"path":"/v2/"},{"backend":{"serviceName":"harbor-harbor-core","servicePort":80},"path":"/chartrepo/"},{"backend":{"serviceName":"harbor-harbor-core","servicePort":80},"path":"/c/"}]}},{"host":"notary.mylabs.dev","http":{"paths":[{"backend":{"serviceName":"harbor-harbor-notary-server","servicePort":4443},"path":"/"}]}}],"tls":[{"hosts":["core.mylabs.dev"],"secretName":"ingress-cert-production"},{"hosts":["notary.mylabs.dev"],"secretName":"ingress-cert-production"}]}}
nginx.ingress.kubernetes.io/proxy-body-size: 0
nginx.ingress.kubernetes.io/ssl-redirect: true
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal CREATE 3m28s nginx-ingress-controller Ingress harbor-system/harbor-harbor-ingress
Normal UPDATE 3m8s nginx-ingress-controller Ingress harbor-system/harbor-harbor-ingress
Open the https://core.mylabs.dev:
Log in:
- User:
admin - Password:
admin
You should see the Web UI: