-
Notifications
You must be signed in to change notification settings - Fork 88
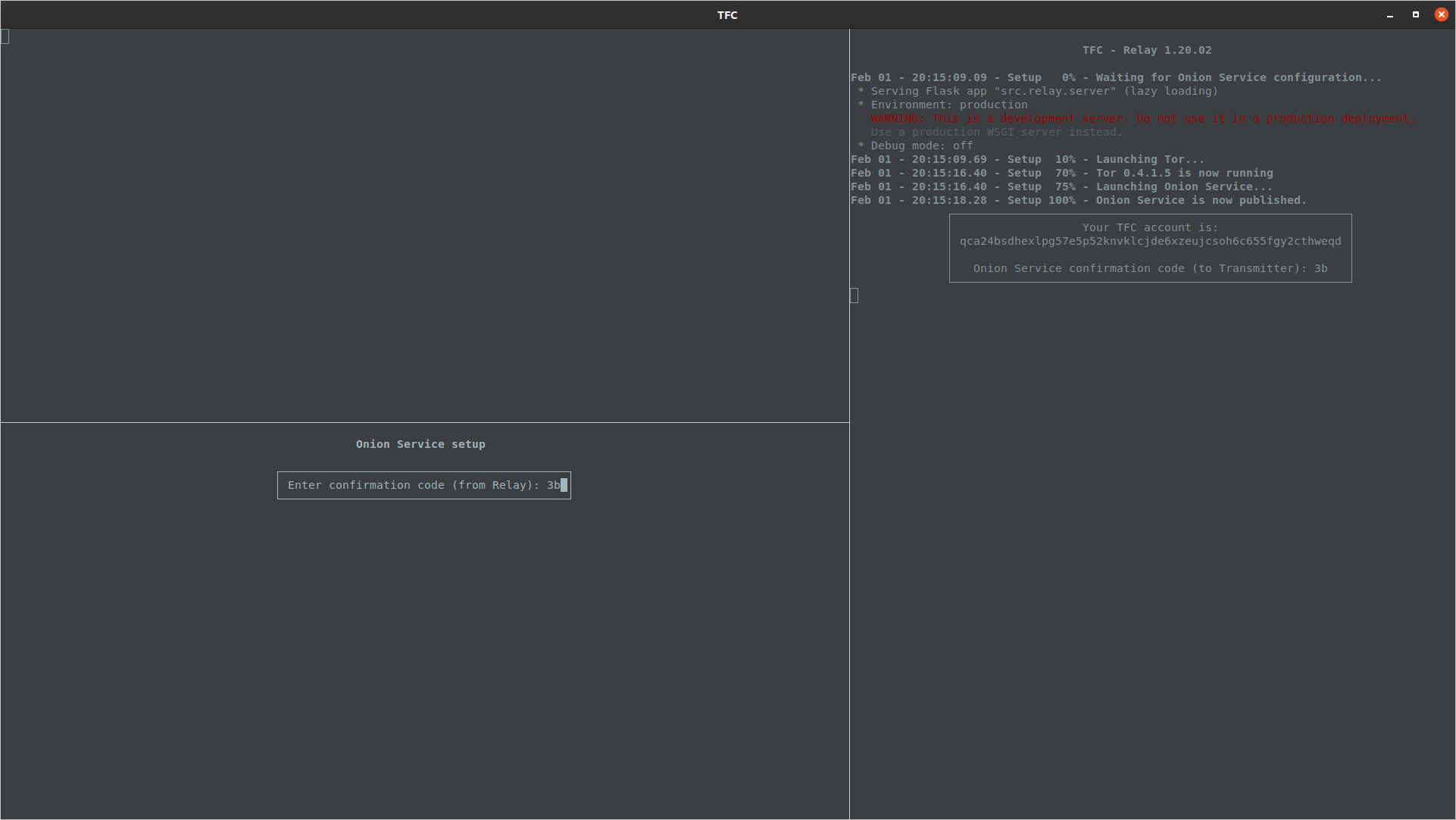
Onion Service Setup
After the master password is set, Transmitter Program creates an ed25519 private key and stores it into a dedicated database. This private key will be automatically exported to the Relay Program on Networked Computer at the start of every session. This private key will be used to start the Tor Onion Service. If the user has any existing contacts, the TFC accounts are also sent to the Relay Program so it can connect to the contacts.
Once the Onion Service data is received, Relay Program will launch Tor and the Onion Service. Once the Onion Service is up, Relay Program displays the user their TFC account (onion URL without http:// prefix and .onion suffix).

Relay Program will also show a confirmation code to the user that they must type to the Transmitter Program. Once the confirmation code has been entered, Transmitter Program allows the user to proceed to the next step.
The depicted Flask warning about "using development server in a production environment" is not a problem in an application such as TFC, where the number of connections is measured in hundreds at most, not thousands or millions web servers often need to scale to.
The TFC account is again, the address of the Onion Service. It is practically impossible to guess or find amidst all the possible TFC accounts. However, if someone knows your TFC account, they are able to see when your Relay Program is running, i.e. when you are online. This does not leak any other information like who you talk to, however. In future, TFC will have better control over who can see when your Relay Program is online with something called prop224 client authorization.