-
Notifications
You must be signed in to change notification settings - Fork 9
User guide
NERD (Network Entity Reputation Database) is a service which aims to gather, aggregate and provide all the available information about known malicious network entities (mostly IP addresses).
The primary way to use NERD is via its web interface. The one of the main NERD instance operated by CESNET is publicly available at https://nerd.cesnet.cz/nerd/ (Note: We are currently not aware of anyone running any other instance.).
There is also an API.
All the data are stored as records with attributes. Each record represents data known about a single entity - an IP address, autonomous system number (ASN), etc.
A record of an IP address contains, for example:
- meta data about detected security events, such as number of events per day and category
- hostname associated with the IP address
- geolocation information
- whether the IP address is listed on some of the public blacklists
- summary score
- timestamp of addition of the address to database (i.e. first seen as malicious), time of last events, etc.
Generally, a record is created for each entity which is reported as malicious by some of the primary data sources.
Currently, the only primary data source is Warden, a community-based alert sharing system operated by CESNET. Data in Warden comes mostly from various IDS systems, honeypots and from a darknet, so they mostly report IP addresses actively trying to find and compromise other systems. Only IP address records are created this way.
For each record, a number of other attributes are fetched from external sources (secondary data), such as the hostname, blacklist presence, etc.
There are also auxiliary records for other types of entities - BGP prefixes and ASNs to capture routing information and IP blocks and organizations to represent data from whois databases.
All the data are periodically updated.
Detailed information about the data model and attributes currently used can be found there: Data model, Attributes
The interface is quite simple - it allows to search IP address records in the database and to see details of individual records.
The main page allows to search and sort IP addresses by various criteria. By default, top 20 addresses with the worst reputation score are shown.
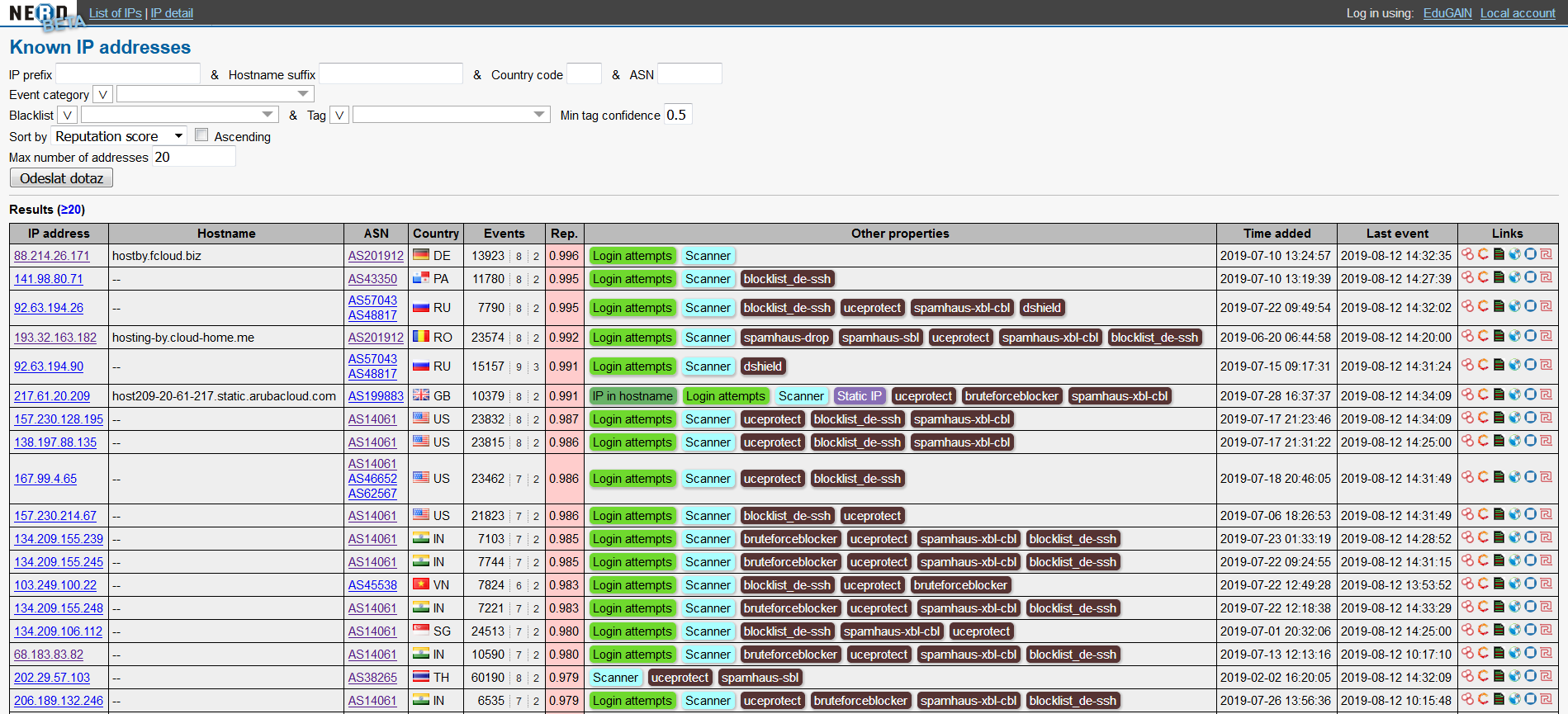
On the top of the page, there is a form to specify search criteria:
- IP address prefix/subnet (e.g.
198.51.100.0/24). - Hostname suffix (e.g.
.example.com) to search by hostname (PTR record in public DNS). - Country (2-letter code by ISO-3166-1, e.g.
CZ). - Autonomous system number (e.g.
AS2852). - Category of a Warden event by which the IP address was reported.
Multiple values can be selected, the button on the left specifies whether any (
⋁, "or") or all (⋀, "and") of them apply. Description of Warden categories can be found here. - Warden node that reported the IP address (visible to trusted partners only, as node names are anonymized for public).
- Blacklist(s) the IP address is listed on.
- Tags assigned to the IP address record.
There is also a possibility to sort results by a specific field and to select the number of results.
If there is at least one record matching the search criteria, a table with results is shown below the form when the query is submitted.
The table contains the IP address, hostname, ASN, country, total number of events (and number of reporting nodes and number of categories) in the last 90 days, reputation score, which summarizes the other data into a number, various tags and presence on blacklists, timestamps of record creation (i.e. first event) and last event, and quick links to search the IP address in several other services.
The IP address on the left is a link to the page with detail of the corresponding record.
The IP detail page shows all the information stored about the IP address in the database.

The page has a simple layout - below the header with the IP address, reputation score and hostname, there is a list of all attributes in the record and their values.
Some of the attribute values are rendered in a special way (e.g. events, blacklists, geolocation, tags) to improve readability, others are shown just as a simple value, as stored in database (either because no special rendering is needed, or because a new data source was added recently and no rendering code for corresponding attribute(s) was added yet).
The events attribute shows a detailed list of event meta-information - number of events per day, category and reporting node (for up to 90 days in past).
The boxes on the right show some information from external systems which are not stored in NERD. These are fetched at the time the page is loaded.
Currently, there are information on open ports from Shodan and data from CESNET's Passive DNS system (which shows history of related DNS records as seen at CESNET's nameservers, namely A records associated with the IP address).
When the user is logged in with a privileged account, a list of the last 100 related Warden events is loaded and shown at the bottom of the page.

The IP detail page contains links to records of other entity types - BGP prefixes, ASNs, IP blocks and organizations. They mostly contain just basic identifying information, since they mostly serve to capture relationships between those entities - i.e. under which BGP prefixes and ASNs are the IP addresses announced to be originated from (according to whois.cymru.com), and to which organization and which IP block the address belong to according to RIR's whois databases (querying whois servers directly).
The only additional information is stored in ASN records.
They contain a BGP rank value provided by CIRCL (see bgpranking.circl.lu)
and a similar rank provided to us by The Email Laundry (eml_rank).
The following scheme shows how different entity records are interconnected:

Most of the data are visible without the need of a user account. However, some bits of information are visible to trusted partners only. To see them, one needs to be logged in under a user account with corresponding privileges set.
An account is also needed to access the API.
Currently, the accounts must be created manually by the system administrators - contact us if you need an account.